no description
http://blog.csdn.net/boat1980/archive/2008/07/23/2698318.aspx
<head>
<script>
function overlay() {
el = document.getElementById("overlay");
el.style.visibility = (el.style.visibility == "visible") ? "hidden" : "visible";
}
</script>
<style>
body {
height:100%;
margin:0;
padding:0;
}
/*外層全部*/
#overlay{
visibility: hidden;
position: absolute;
left: 0px;
top: 0px;
width:100%;
height:100%;
text-align:center;
z-index: 1000;
background-color:#000;
filter: alpha(opacity=70); /*ie支持的半透明,下面兩名為ff支持的*/
-moz-opacity: 0.7;
opacity:.70;
}
/*外層的顯示區(qū)*/
#overlay div {
width:300px;
margin: 100px auto;
background-color: #FFFFFF;
border:1px solid #000;
padding:15px;
text-align:center;
}
</style>
</head>
<body id="body">
<div id="overlay">
<div>
用戶名:<input type="text" name="" /><br/>
密 碼:<input type="text" name="" /><br/>
<input type="button" value="關(guān)閉" onclick="overlay()" />
</div>
</div>
<a href='#' onclick='overlay()'>Click here to show the overlay</a>
</body>
</html>
result raw(2000);
l_mod number := dbms_crypto.ENCRYPT_3DES+dbms_crypto.CHAIN_ECB+dbms_crypto.PAD_PKCS5;
begin
result := dbms_crypto.Encrypt(src => utl_i18n.string_to_raw('wwww'),typ => l_mod,key => hextoraw('123456789012345678901234567890123456')
);
dbms_output.put_line(result);
end;
/
二,摘要
dbms_crypto.Hash(utl_i18n.string_to_raw('input'),dbms_crypto.MD5))
用了幾天jira管理對它的權(quán)限模式有了初步理解:
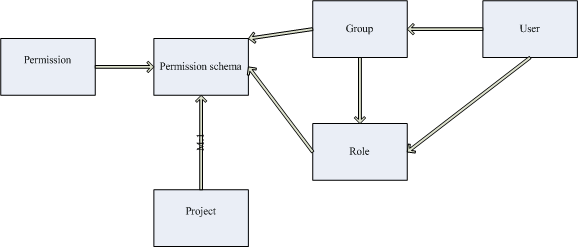
project和permission schema多對一,從而形成了permission schema的重用
而permission schema本身則代表了group/user和pemission之前的映射關(guān)系
另外,jira還有一個Project Role的概念更增加了jira權(quán)限管理的靈活性
其實(shí)它實(shí)質(zhì)上就是一個角色(RBAC中的R),可以和group/user多對多關(guān)聯(lián),
(當(dāng)然也可和Permission通過schema進(jìn)行關(guān)聯(lián))
使jira的權(quán)限配置更新靈活的同時,也增加了相當(dāng)?shù)膹?fù)雜性
一,造libmysql.def文件
1, ${mysql_home}/include/libmySQL.def文件如果有直接用
2, 否則下載pexports工具,執(zhí)行pexprots libmySQL.dll> libmySQL.def(libmySQL.dll在${mysql_home}/bin目錄下一般會有)
二,轉(zhuǎn)換成靜態(tài)庫
dlltool --input-def libmySQL.def --dllname libmySQL.dll --output-lib libmysql.a -k
三,配置Eclipse(靜態(tài)庫和動態(tài)庫加法都是-L${DIR} -l${libname},但誰的優(yōu)先級高呢?)
1, 加上庫目錄,如"${workspace_loc:/hello_mysql/libs}"
2, 加上libmysql.a的庫名: mysql
3, 構(gòu)建,報錯: #ff0000 reference to `mysql_real_connect@32'之類的錯
4, 修改def文件,將mysql_real_connect改成mysql_real_connect@32,其它錯誤同理,并重新生成靜態(tài)庫
5, 重新構(gòu)建完成
四,示例程序(只須修改連接信息及表名)
/*下面這一行一定要加上*/
#include <my_global.h>
#include <mysql.h>
int main() {
MYSQL mysql;
MYSQL_RES *result;
MYSQL_ROW row;
int numrows, numcols, c;
mysql_init(&mysql);
if (!mysql_real_connect(&mysql, "localhost", "opencart", "opencart", "opencart", 0, NULL, 0)) {
fprintf(stderr,"Failed to connect to database: Error %d:%s\n", mysql_errno(&mysql), mysql_error(&mysql));
}
char query[] = "SELECT * FROM product";
if (mysql_query(&mysql, query))
{
fprintf(stderr,"Error executing query: Error %d: %s\n", mysql_errno(&mysql), mysql_error(&mysql));
}
result = mysql_use_result(&mysql);
if (!result) {
fprintf(stderr,"Error executing query: Error %d: %s\n", mysql_errno(&mysql), mysql_error(&mysql));
}
numcols = mysql_num_fields(result);
while (row = mysql_fetch_row(result)) {
for (c = 0; c < numcols; c++) {
printf("%s\t", row[c]);
}
printf("\n");
}
}
一、安裝
1, 安裝xampp
2, 安裝zend studio[6]
二、配置調(diào)式
1,在http.conf中指定php.ini的位置
PhpIniDir "D:/xampp/php"
2, 在php.ini中的zend的部分指定以下內(nèi)容(ZendDebugger.dll是從zend studio中搜出來的)
[Zend]
zend_extension_ts = "D:\xampp\php\zendOptimizer\lib\ZendDebugger_5.2.12.dll"
;下面部分可選
zend_debugger.allow_hosts=127.0.0.1/32,127.0.0.1/24
zend_debugger.expose_remotely=allowed_hosts
放在/usr/local/bin下,挺好用
# this script converts an rpm into a plain tarball
mkdir $$.cpio
rpm2cpio $@ > $$.cpio/foo
cd $$.cpio
cpio -i -m -d < foo
rm -f foo
find . -type d -perm 700 -exec chmod 755 {} \;
tar cvzf ../`basename $@ .rpm`.tar.gz .
cd ../
rm -rf $$.cpio
1,去http://rpm.pbone.net/下載下列rpm包并安裝
libnasl-2.2.9-1.fc5.i386.rpm
nessus-core-2.2.9-1.fc5.i386.rpm
nessus-core-debuginfo-2.2.9-1.fc5.i386.rpm(可選)
nessus-libraries-2.2.9-1.fc5.i386.rpm
nessus-server-2.2.9-1.fc5.i386.rpm
nessus-gui-2.2.9-1.fc5.i386.rpm
2, 找個能用的郵箱去http://www.nessus.org/plugins/index.php?view=register注冊一下
3, 按郵件中的方式運(yùn)行nessus-fetch --register ****
4, 運(yùn)行nessus-adduser增加一個沒有rule的用戶
5, 運(yùn)行nessus-mkcert造個證書
6, 運(yùn)行nessus-fetch --check檢查一下狀態(tài)
7, 如果前面沒啥問題,運(yùn)行service nessusd start
如果這一步除了成功沒啥別的輸出就ok啦
限制本機(jī)的對外訪問(例如不讓測試環(huán)境訪問生產(chǎn)庫):
iptables -t filter -A OUTPUT -d 192.168.2.2 -p tcp --dport 1521 -j REJECT
#端口轉(zhuǎn)發(fā)到另一臺機(jī)器上
-A PREROUTING -d $ip1 -i eth0 -p tcp -m tcp --dport $port1 -j DNAT --to-destination $ip2:$port2
-A POSTROUTING -d $ip2 -p tcp -m tcp --dport $port2 -j SNAT --to-source $ip1
#本機(jī)端口相互映射
-A PREROUTING -p tcp --dport $port1 -j REDIRECT --to-port $port2
pre-commit.tmpl,然后更名pre-commit并加上執(zhí)行權(quán)限:
REPOS="$1"
TXN="$2"
RES="OK"
# Make sure that the log message contains some text.
SVNLOOK=/app/subversion/bin/svnlook
$SVNLOOK log -t "$TXN" "$REPOS" | egrep "[^[:space:]]+" >/dev/null || unset RES
if [ "$RES" != "OK" ]
then
echo "You must input some comments for you commit" >&2
exit 1
fi
# All checks passed, so allow the commit.
exit 0
fisheye(1.4.3):
cenqua_com_licensing.atlassian.license.DefaultLicense
isExpired(),getExpiryDate()
cenqua_com_licensing.atlassian.license.DefaultLicenseType(重點(diǎn))
isEvaluationLicenseType(),expires().....
一,將pem格式的key文件導(dǎo)入keystore
摘抄備用:http://www.agentbob.info/agentbob/79-AB.html
說明: 經(jīng)試驗(yàn)證書的pem文件可能通過keytool直接導(dǎo)入keystore中的
Apache Tomcat and many other Java applications expect to retrieve SSL/TLS
certificates from a Java Key Store (JKS). Jave Virtual Machines usually come
with
keytool  to help you create a new key store.
to help you create a new key store.
Keytool helps you to:
- create a new JKS with a new private key
- generate a Certificate Signung Request (CSR) for the private key in this JKS
- import a certificate that you received for this CSR into your JKS
Keytool does not let you import an existing private key for which you already have a certificate. So you need to do this yourself, here's how:
Let's assume you have a private key (key.pem) and a certificate (cert.pem), both in PEM format as the file names suggest.
PEM format is 'kind-of-human-readable' and looks like e.g.
-----BEGIN CERTIFICATE-----
Ulv6GtdFbjzLeqlkelqwewlq822OrEPdH+zxKUkKGX/eN
.
. (snip)
.
9801asds3BCfu52dm7JHzPAOqWKaEwIgymlk=
----END CERTIFICATE-----
Convert both, the key and the certificate into DER format using
openssl  :
:
openssl pkcs8 -topk8 -nocrypt -in key.pem -inform PEM -out key.der -outform DER
openssl x509 -in cert.pem -inform PEM -out cert.der -outform DER
Now comes the tricky bit, you need something to import these files into the JKS. ImportKey will do this for you, get the ImportKey.java (text/x-java-source, 6.6 kB, info) source or the compiled (Java 1.5 !) ImportKey.class (application/octet-stream, 3.3 kB, info) and run it like
user@host:~$ java ImportKey key.der cert.der
Using keystore-file : /home/user/keystore.ImportKey
One certificate, no chain.
Key and certificate stored.
Alias:importkey Password:importkey
Now we have a proper JKS containing our private key and certificate in a file called keystore.ImportKey, using 'importkey' as alias and also as password. For any further changes, like changing the password we can use keytool.
二、將私鑰導(dǎo)出成pem文件(默認(rèn)keytool是不能導(dǎo)出私鑰的)
import java.security.cert.Certificate;
import java.security.*;
import java.io.File;
import java.io.FileInputStream;
class ExportPriv {
public static void main(String args[]) throws Exception{
ExportPriv myep = new ExportPriv();
myep.doit();
}
public void doit() throws Exception{
KeyStore ks = KeyStore.getInstance("JKS");
String fileName = "store.jks";
char[] passPhrase = "password".toCharArray();
BASE64Encoder myB64 = new BASE64Encoder();
File certificateFile = new File(fileName);
ks.load(new FileInputStream(certificateFile), passPhrase);
KeyPair kp = getPrivateKey(ks, "alias", passPhrase);
PrivateKey privKey = kp.getPrivate();
String b64 = myB64.encode(privKey.getEncoded());
System.out.println("-----BEGIN PRIVATE KEY-----");
System.out.println(b64);
System.out.println("-----END PRIVATE KEY-----");
}
// From http://javaalmanac.com/egs/java.security/GetKeyFromKs.html
public KeyPair getPrivateKey(KeyStore keystore, String alias, char[] password) {
try {
// Get private key
Key key = keystore.getKey(alias, password);
if (key instanceof PrivateKey) {
// Get certificate of public key
Certificate cert = keystore.getCertificate(alias);
// Get public key
PublicKey publicKey = cert.getPublicKey();
// Return a key pair
return new KeyPair(publicKey, (PrivateKey)key);
}
} catch (UnrecoverableKeyException e) {
} catch (NoSuchAlgorithmException e) {
} catch (KeyStoreException e) {
}
return null;
}
}



